
Objectives of the service
All the aeronautical European development plans suggest a vast diffusion and application of RPAS in several industrial areas, from land monitoring to zones patrolling. The integration of RPAS in a non-segregated airspace sets some challenges related to cyber-attack risk assessment. Cyber-attacks can affect operation and airspace safety or seriously injure people and damage property. CRUISE’s intent is to design, develop and validate a CyberSec Test Range in the Grottaglie Airport, that already experiments RPAS and studies the integration of UAS in non-segregated airspace, a place where the overall assessment on vulnerability and resilience of UAS with respect to cyber-attacks can be led. The Test Range, combining ICT systems, SATCOM and EO services, will aim at evaluating the overall vulnerability of UAS, including the analysis of flight platforms, on board avionics and payload sensors. Quality, consistency and integrity of data collected during VLOS, RLOS, BRLOS operations will be verified. The following categories of cyber-attacks will be assessed
-
Hardware attacks – the hacker has direct access to the RPAS;
-
Wireless attacks – the hacker uses wireless communication in order to attack command, control and communication systems;
Sensor Spoofing – The hacker substitutes real data collected by the on-board sensors with fake data
Users and their needs
The main benefit that users and customers obtain from the exploitation of CRUISE and CyberSec Test Range results is the possibility to validate their own aeronautical products (avionics, payload…) or to individuate sources of risk (Point of Penetration) in the system and therefore fix them. CRUISE offers the possibility to verify whether an RPAS can withstand attacks to payload data or to the geolocation system. Such benefits can be obtained in design phase or during the development of composing architectures of the UAS platform thus evaluating cyber-vulnerability in a simulated environment, through an emulation system or through real flight tests. These benefits can be spread to producers of onboard avionic devices (SATCOM devices, software systems…) as well as air systems integrators.
At the same time, end users of aerial services (i.e., civil protection agencies, municipalities, …) can be assured about quality and trustfulness of data collected with RPAS missions.
Service/ system concept
The customer will receive reports generated during the data analysis phase; specifically, the report will present:
-
the identified Point(s) of Penetration will be proposed to user
-
an evaluation of the potential attacks that could exploit them,
-
the risks for the platform and for the operation in case of attack.
Service evaluation feedback is requested so to improve system performances and/or service portfolio. At the meantime a vulnerabilities mitigation guideline can be provided to the users, if required.
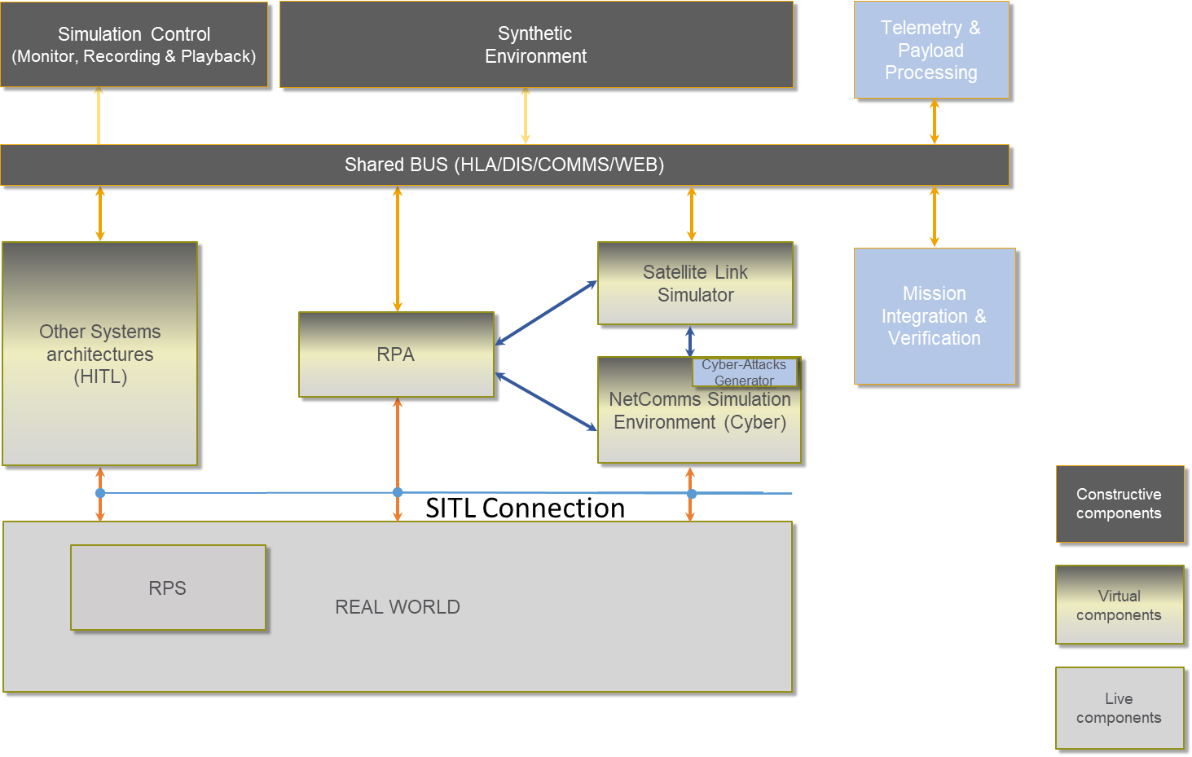
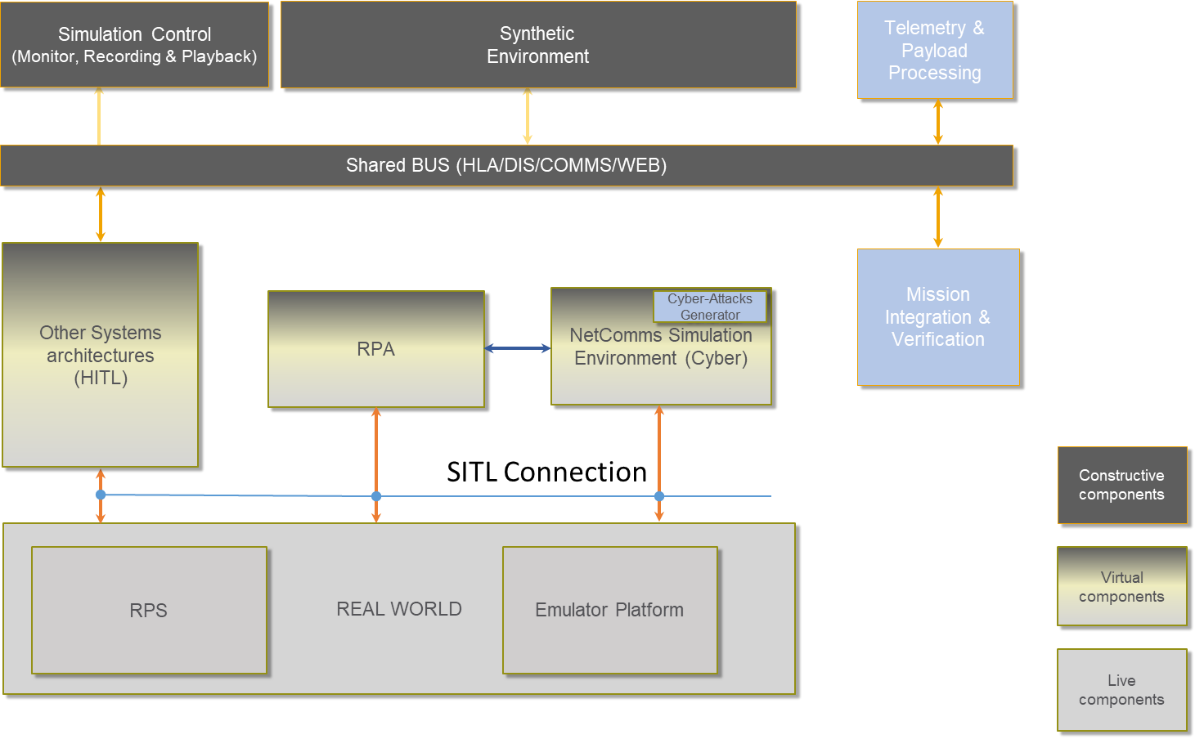
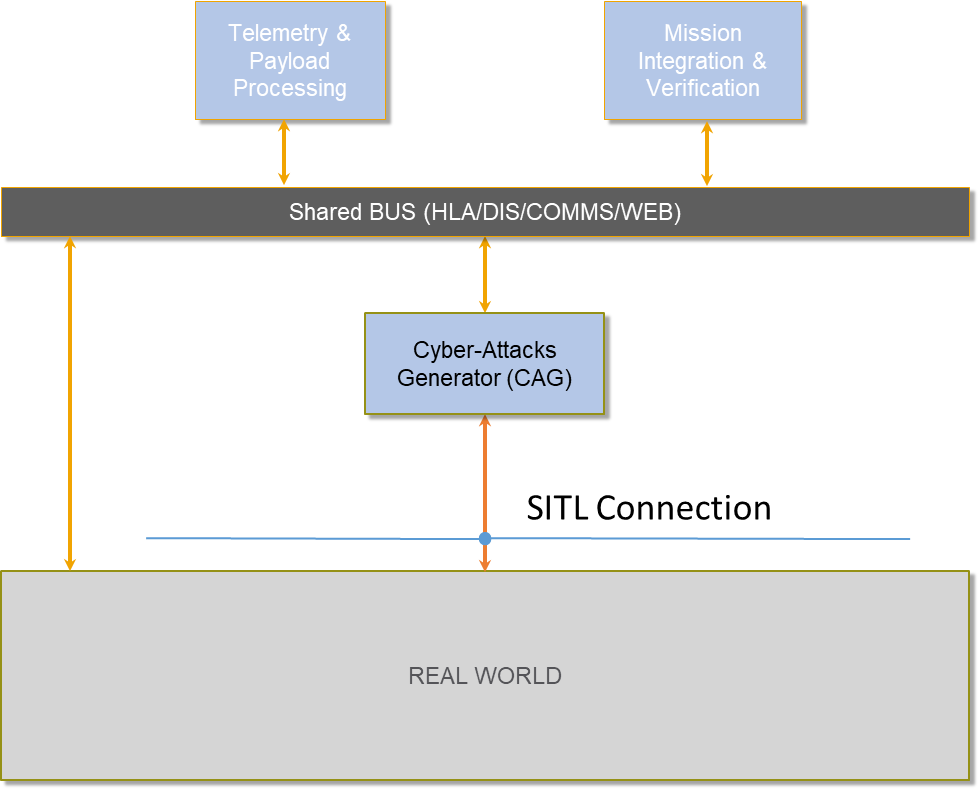
Depending on the different test scenarios, three architectures compose the Cybersec Test Bed: Simulation and emulation environments, and real flights.
Space Added Value
CRUISE architecture relies on Satellite telecommunication services (SatCom), Earth Observation (EO) (i.e. Copernicus, COSMO-SkyMed).
Satcom is used for telecommunication in support of both UAS Command, Control (C2) and ATC (C3) and payload communication channel in case of Beyond Radio Line of Sight operations. EO is used in support of mission simulation system, preparation phase, in real environment (as an on-board countermeasure technique to assess EGNSS performance comparing acquired data with EO) and to report the performances and validate the mission.
Added-value, of using the above different space assets, shared with terrestrial assets are:
-
Non-invasiveness;
-
Command and control in extended scenarios – from LOS to BRLOS
-
ATM in extended scenarios – from LOS to BRLOS
-
Surveillance and monitoring data gathered in extended scenarios – from LOS to BRLOS
-
Vulnerability and risk assessment in simulations environment with geo-references data of real mission area.
-
Global coverage
Current Status
The project started on January 2019, and the first phase, focused on CyberSec Test Range design and business modelling, was closed on November 2019. The second phase of the project focused on detailed design, implementation and deployment, ended in June 2023.






